
Steganography with encrypted containers
Steganography with an encrypted file container + hidden volume.
I’ve always been intrigued by steganography, hiding messages in data. Take an instance were two spies are out in the field separated by a decent distance, not feasible to travel. They are not always “being watched” but have scrutinized communication lines and desperately need to talk to each other. Each of them are trained highly in technical skills and they feel the best option is to hide messages but in plain sight.
One of them gets caught sending secret messages and is forced to reveal the password to their encrypted container. You give them the one to the outer shell, but not the hidden volume.
For the purpose of this steganography demonstration I will be creating an encrypted container which also contains a secondary hidden volume. This encrypted container with a hidden volume will then be inserted into an MP4 file.
If you want to try this you will need something to make an encrypted container, I’m using VeraCrypt for this demonstration. You can download it here. You will also need to obtain software capable of doing steganography, such software can be written by good programmers or downloaded. The script I am using I feel is proprietary in the sense that it was given to me and I was never told I could freely distribute, so I wont. Steganography software is available online for download you can go look or …look here.
To create an encrypted container with a hidden volume in VeraCrypt the process is easy, I will walk you through the steps.
- Start up VeraCrypt, make sure it’s not the VeraCrypt Expander.
- Click the Create Volume button.
- Check the radio button that says Create an encrypted file container.
- THIS IS IMPORTANT- Make sure you select the radio button that says Hidden VeraCrypt Volume.
- Select Normal Mode.
- Choose a location for the container, just so you don’t loose it….click Select File, navigate to your Desktop and in the file explorer window click New Folder or Create New Folder. Name it something …anything will do for this experiment.
- Go into the folder you just created and then in the File Name text box give your encrypted container a name and click save and then click next in the VeraCrypt window.
- Next you should be in a window where you can choose the encryption algorithm, by default it is set to AES and we can leave it that way. You may however want to select a stronger hash algorithm, in the drop down menu select SHA-256.
- Enter the size you wish your Main (Outer Shell) container to be. NOTE: THIS WILL IMPACT THE SIZE OF YOUR HIDDEN VOLUME. For the purpose of this demonstration (and to be most realistic) I created a small hidden volume. You can choose whatever size you want but because I will be hiding this container in an MP4 file, I dont want an MP4 file that is 20GB’s large. I chose to use 15MB
- Select a password for your volume, note that this is the password for your outer shell. You will have a second password for your hidden volume. <–DO NOT FORGET THIS.
- When formatting the volume it will ask you to move your mouse around a bit to generate random bits to use in the AES algorithm for the encryption.
- When you’re asked to either open the outer volume or click next, SELECT NEXT. We still need to make our hidden volume.
- After clicking next you will automatically be prompted with the hidden volume setup, the default encryption for this is fine also but again you may want to change the hash algorithm to SHA-256.
- The next window will give you the option to enter your size for the hidden volume. Make careful note of the maximum size possible for hidden volume notification in bold…..
- Click the next button and move the mouse around to generate the random bits and then press format. You should have an encrypted container in the folder you specified earlier.
Choosing a file
Depending on the program you choose to do your stego you may be restricted to certain file types. I am choosing an MP4 because I enjoy music and it is one of the formats that my program can successfully inject. Pay attention to the file formats your program supports before downloading or purchasing software.
The steganography
Unfortunately I am unable to give out this tool but there are many openly available. The program I am using was written in the Python programming language in the 2.7.x version range. I have installed python 2.7.10 and navigated to the Desktop directory in my command line in Windows. To open a command line in Windows you can hit WindowsKey + R to bring up the Run dialog and enter cmd and press enter. To change directories use the cd command.
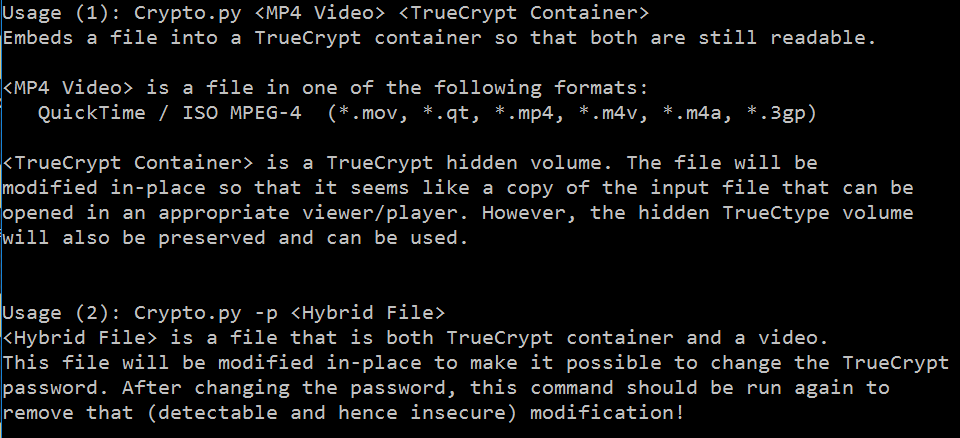
Figure – 1 illustrates the main menu for my steganography tool. Notice that only certain formats are available such as .mov .qt .mp4 .m4v .3gp
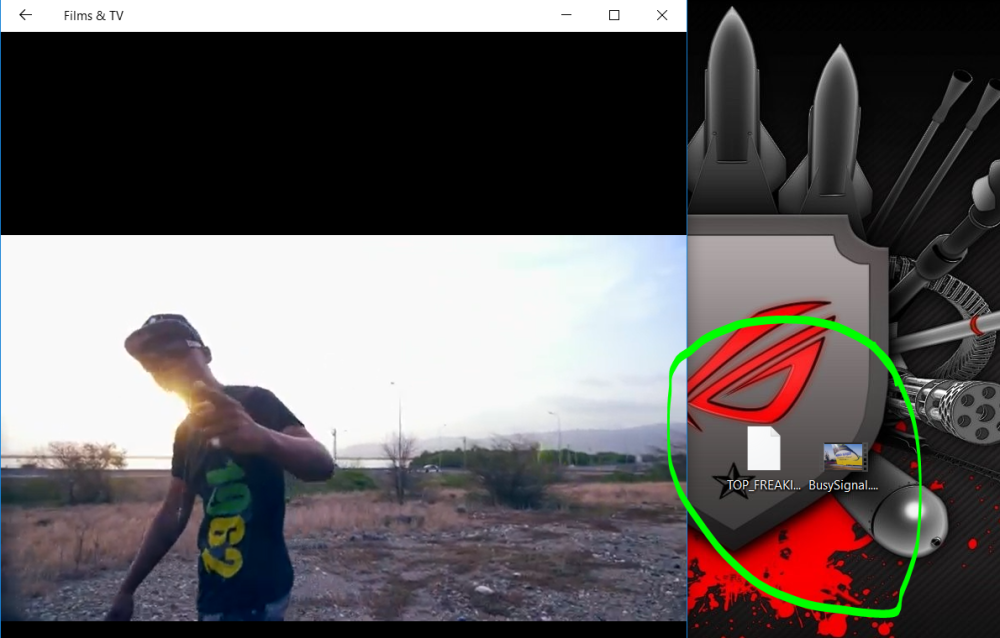
Figure – 2 shows the open (playing) view of the MP4 I choose and circled in green is TOP_FREAKIN_SECRET which is the encrypted container and BusySignal.mp4
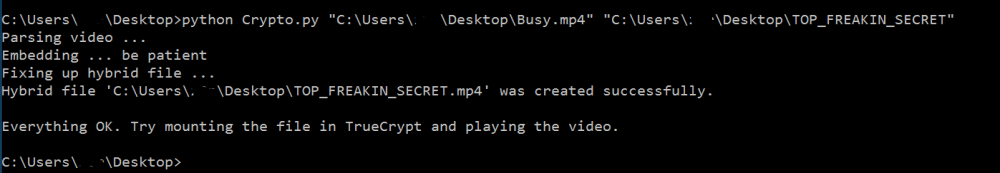
Figure – 3 shows the successful process of running the stego script to inject the encrypted container into the MP4 file.

Figure – 4 shows the MP4 which contains the hidden container adjacent to the legitimate MP4. For obvious reasons, you can change the name of the crafted MP4 to whatever you desire.
Once you successfully perform the steganography aspect you can try to mount the encrypted container, you may either try to mount the outer shell, or the hidden volume. For the purpose of the demo I will re-open the VeraCrypt suite and select a drive letter and then click the select file button. Direct the program to the newly generated stego file and click mount. A password prompt should appear and this gives you the options to enter the outer shell password OR the hidden container password. For this demonstration I will enter the password for the hidden container.
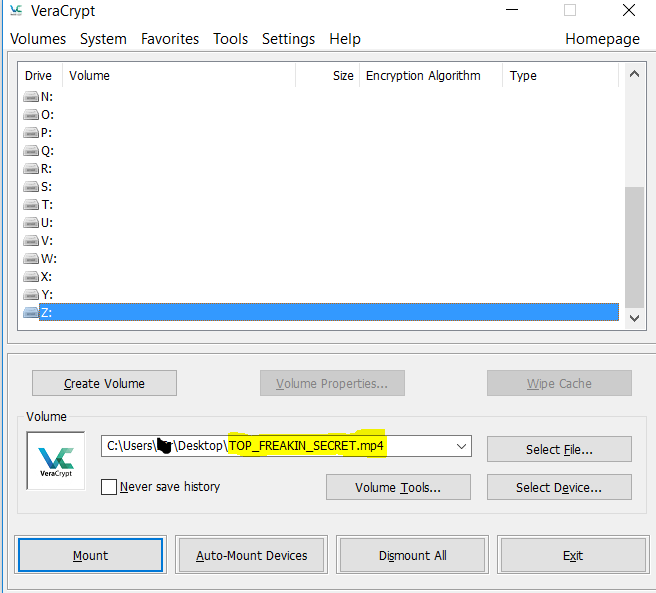
Figure – 5 shows selecting the drive letter :Z and directing the VeraCrypt suite to open the encrypted container which after the steganography is in an MP4 file. Note the file extension.
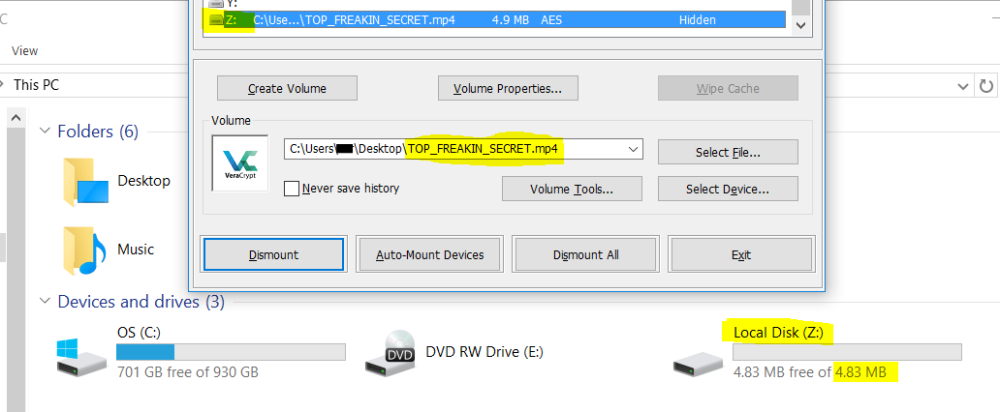
Figure – 6 shows the TOP_FREAKIN_SECRET.mp4 file mounted as an encrypted container.
This whole process (without writing a blog post while doing it) takes about 10 minutes. It is an amazing piece of trickery that I enjoy reading about and playing with. I encourage you to do the same.
P.S. Yes the file still plays.